In the Internet age, developers increasingly interact with network data. Just as we rely on the debugging features of our IDEs to optimize our code, network debugging tools have become indispensable assistants for quickly, efficiently learning, researching, and analyzing network data. This article explains how to use Proxyman to capture the network request information of an iPhone app and simulate server responses by providing mock data. This allows you to test and develop applications without relying on a real server.
Background and Requirements
Recently, while using an iPhone app purchased from the App Store, I stumbled upon an interesting phenomenon: the app triggered a unique UI response when it received a specific combination of external data. Unfortunately, I was unable to capture a screenshot at that time, and the data combination did not appear again during subsequent uses. To reproduce this special effect, I decided to take a more proactive approach—intercepting and modifying the app’s network data by providing mock data.
There are many network debugging proxy tools available that can achieve this goal. However, as an active developer within the Apple ecosystem, I chose Proxyman, which runs more smoothly on macOS and integrates better with Apple’s systems.
For privacy protection purposes, all screenshots and rule configurations related to network data in this article are illustrative and do not reflect actual scenarios.
Installing and Configuring Proxyman and Certificates
Overview of Proxyman
Proxyman is a modern network debugging proxy tool designed specifically for capturing, analyzing, and modifying HTTP(S) requests/responses. It supports multiple platforms including macOS, iOS, Windows, Linux, and Android, and is suitable for various scenarios such as web development, mobile app debugging, and API testing.
Basic Configuration
After installing Proxyman on macOS, it is automatically set as the system’s default network proxy. If you normally use other proxy software, please disable them before enabling Proxyman. To avoid forgetting to revert the settings, it is recommended to enable the “Automatically Disable Proxy When App Exits” option in Proxyman’s preferences.
Why Install a Certificate
Most network debugging tools, including Proxyman, use man-in-the-middle (MITM) techniques to intercept and analyze encrypted network data. To establish this “trusted” intermediary identity, you need to install the certificate provided by Proxyman on both your Mac and iPhone.
It is worth mentioning that Proxyman also offers an iPhone app, which allows network debugging directly on the device without relying on macOS. However, considering that analyzing data on a Mac is more convenient, this article adopts the combination of using Proxyman on both the iPhone and Mac.
Certificate Installation Steps
Within the Proxyman interface, click on “Certificate -> Install Certificate on iOS” in the menu bar.
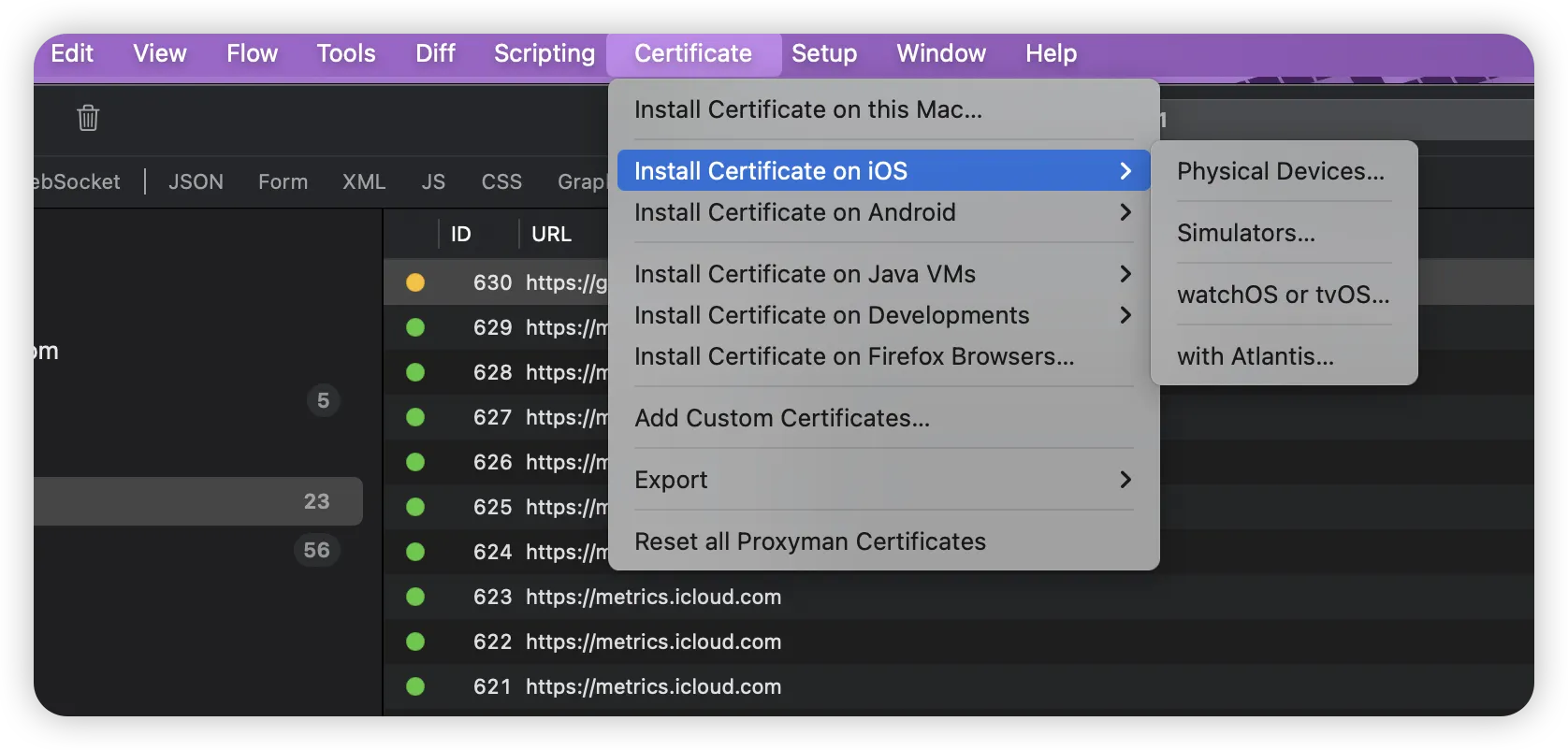
If you have not yet installed the certificate on your macOS device, Proxyman will first guide you through the certificate installation on your Mac.
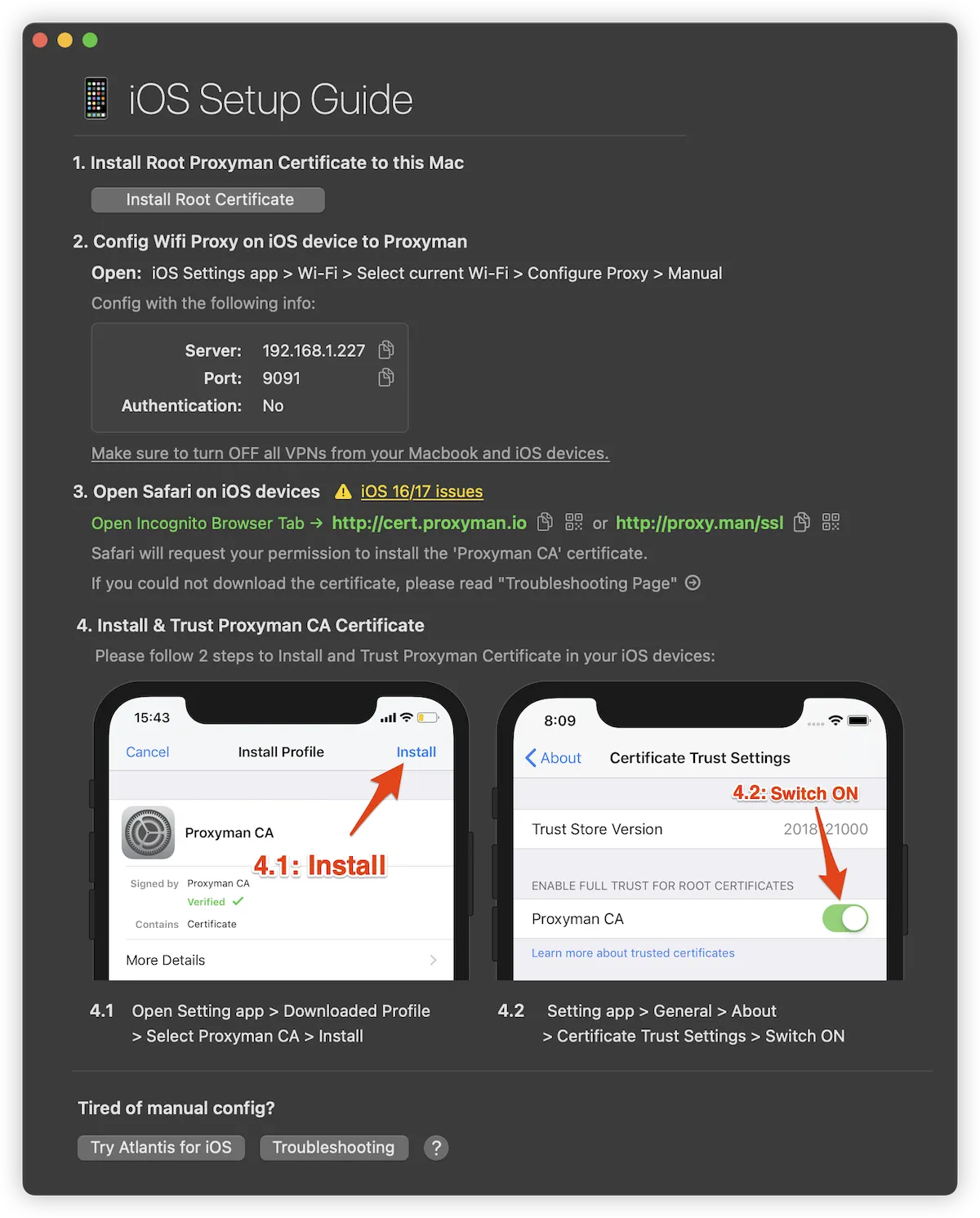
Proxyman’s installation guide is very clear and intuitive. By following the steps, you can easily install the certificates on both devices. The complete process is summarized as follows:
- Install the Proxyman root certificate on your Mac.
- Configure the proxy on your iPhone’s network settings according to the IP address and port number provided by Proxyman.
- Visit
https://cert.proxyman.ioin the iPhone browser to download and install the iOS certificate. - Activate the certificate in the iPhone system settings (Path: Settings -> General -> About -> Certificate Trust Settings).
Precautions
Pay special attention to the following points during the certificate installation process:
- The iOS device must be running iOS 18 or later (versions 16 and 17 have bugs).
- The iPhone and Mac must be connected to the same Wi-Fi network.
- Other network proxies on the iPhone (such as VPN apps) must be disabled.
- Ensure Proxyman is running and that other proxy settings on the Mac are turned off.
- The iPhone certificate must be downloaded through the proxy service provided by Proxyman.
- If the certificate fails to download automatically, try using your browser’s private browsing mode to access the download link.
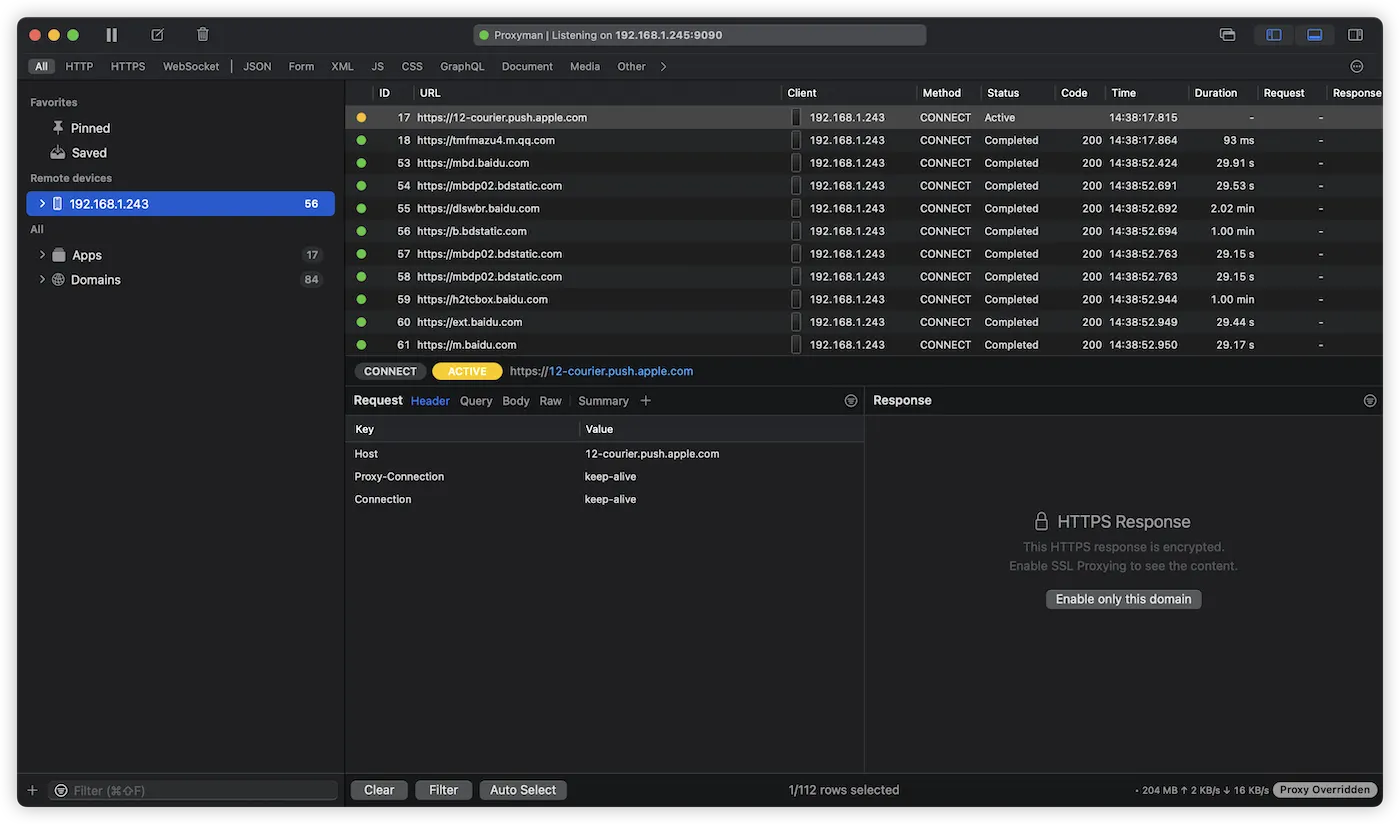
After setting up the proxy on the iPhone (even if the iOS certificate is not yet installed), you will see the network request records from the iPhone in Proxyman’s sidebar, indicating that the basic connection has been successfully established.
Capturing Network Requests
Challenges in Request Identification
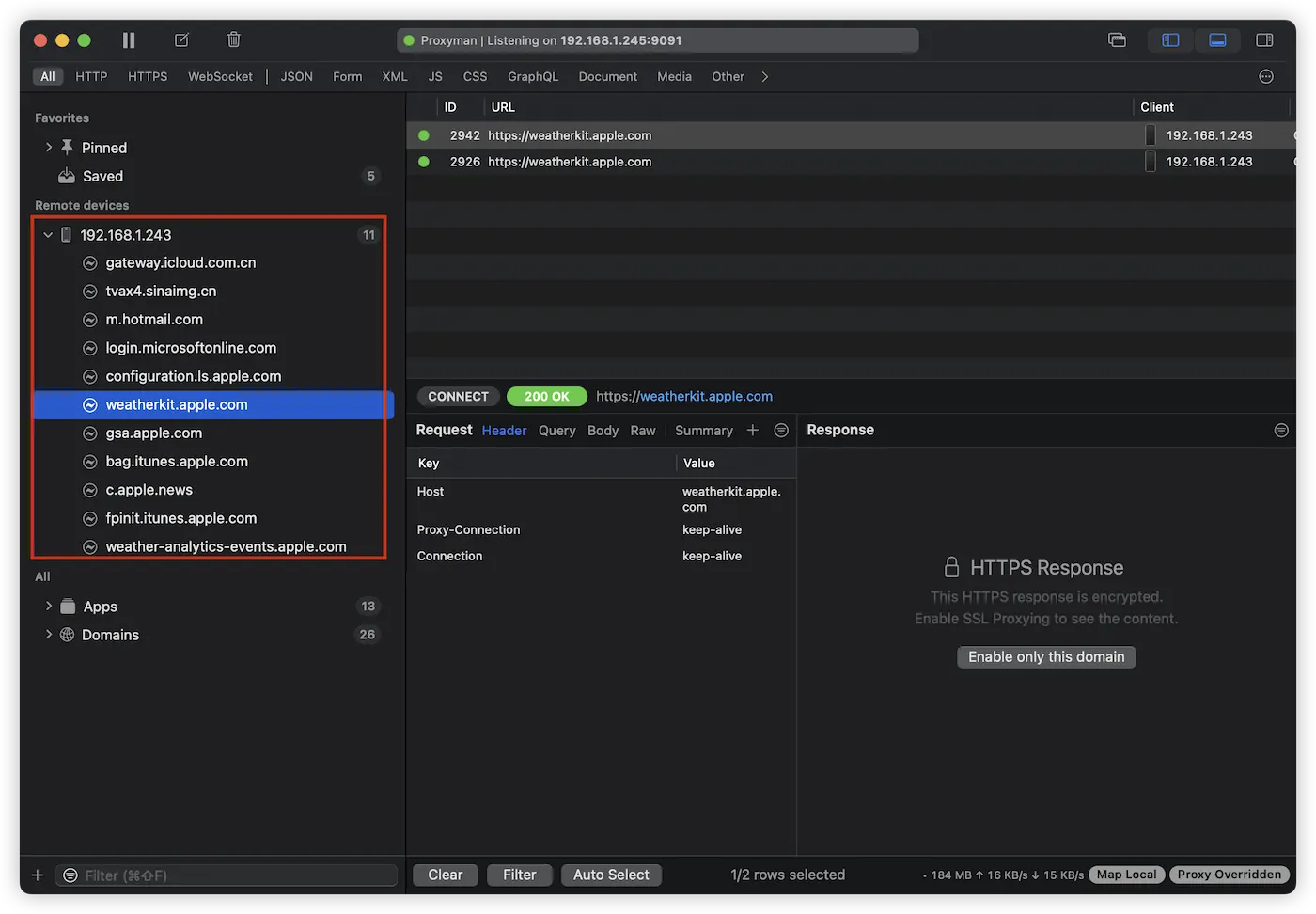
There is a significant difference between capturing network requests from an iPhone app and monitoring local requests on a Mac: Proxyman does not categorize network requests from the iPhone by application (Apps) but rather organizes them by domain (Domains). This makes it relatively complex to identify the network traffic of a specific app.
Compared to analyzing an app on a simulator, a real iPhone device typically generates more background network requests. Therefore, you may need to “cold start” (completely close and reopen) the target app on the iPhone multiple times to accurately identify the network connections associated with that app.
Analyzing Encrypted Traffic
After successfully locating the target connection, if the connection uses SSL/TLS encryption (as most modern apps do), you need to enable the HTTPS parsing proxy function for that specific connection in Proxyman’s Response panel.
- Pro version users can enable parsing for an unlimited number of SSL connections.
- Trial version users can only parse up to two SSL connections at a time (though the connection addresses can be changed at any time).
Viewing Decrypted Data
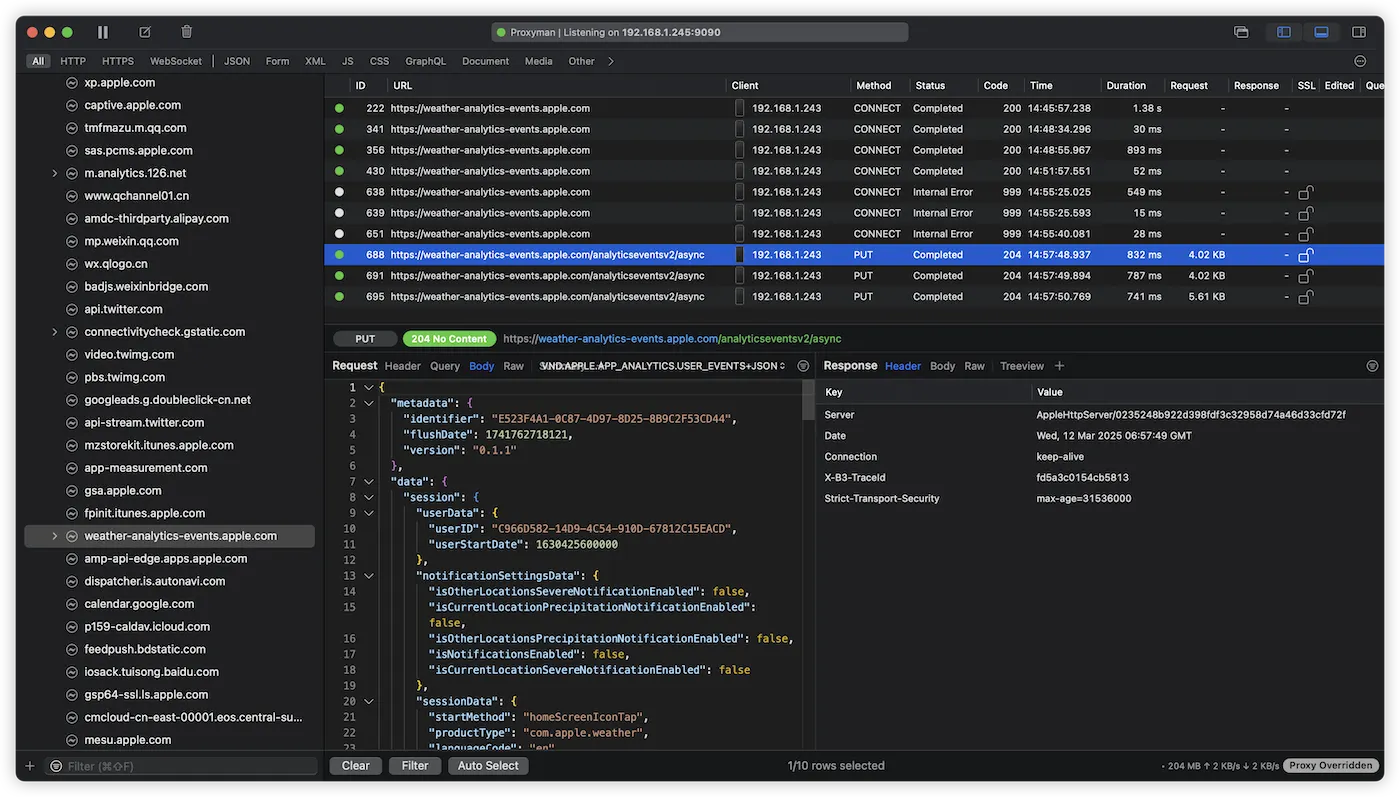
Once HTTPS proxying is enabled, you need to cold start the target app on the iPhone again. When the app re-establishes its network connection, you will notice several changes in the Proxyman interface:
- A “lock” icon appears next to the corresponding network connection entry, indicating that encryption has been successfully removed.
- You will be able to view the complete decrypted network data, including detailed information about both the request and response.
- The data displayed shows the full communication between the app and the server, facilitating further analysis.
This step is a necessary prerequisite for subsequent data simulation (Mock), as effective data analysis and modification can only occur once the encrypted traffic is properly decrypted.
Data Simulation (Mock Data)
What is Mock Data?
Mock data is a network debugging technique that involves precisely matching specific network requests sent by the iPhone app and replacing the actual server response with locally customized data. This technique allows developers to test how the app responds to various data scenarios without modifying the app’s source code.
Creating a Mock Response
Proxyman provides an intuitive interface for setting up and managing mock data. The steps are as follows:
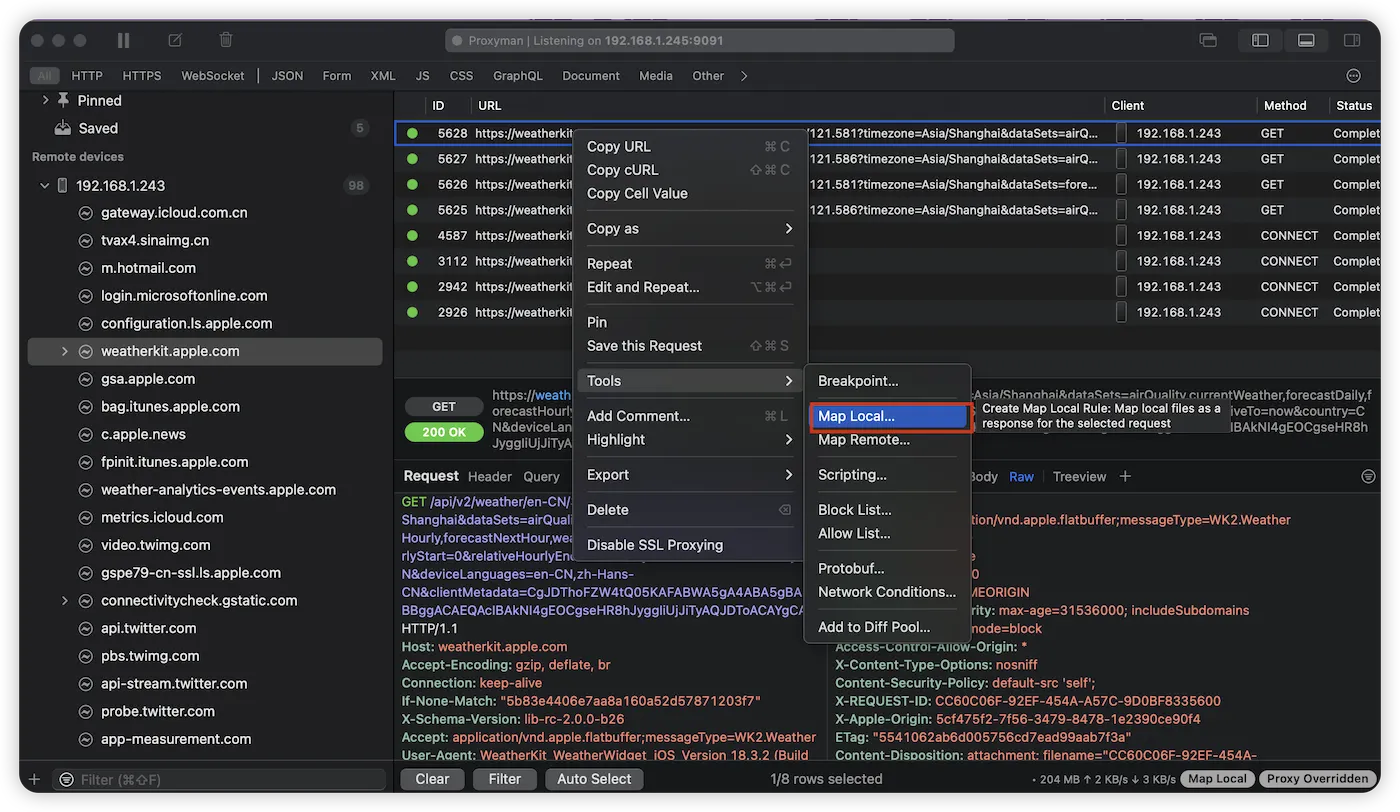
- Locate the target network request in the Proxyman interface.
- Right-click the request and select “Tools -> Map Local” from the context menu.
- The “Map Local Editor” configuration panel will open.
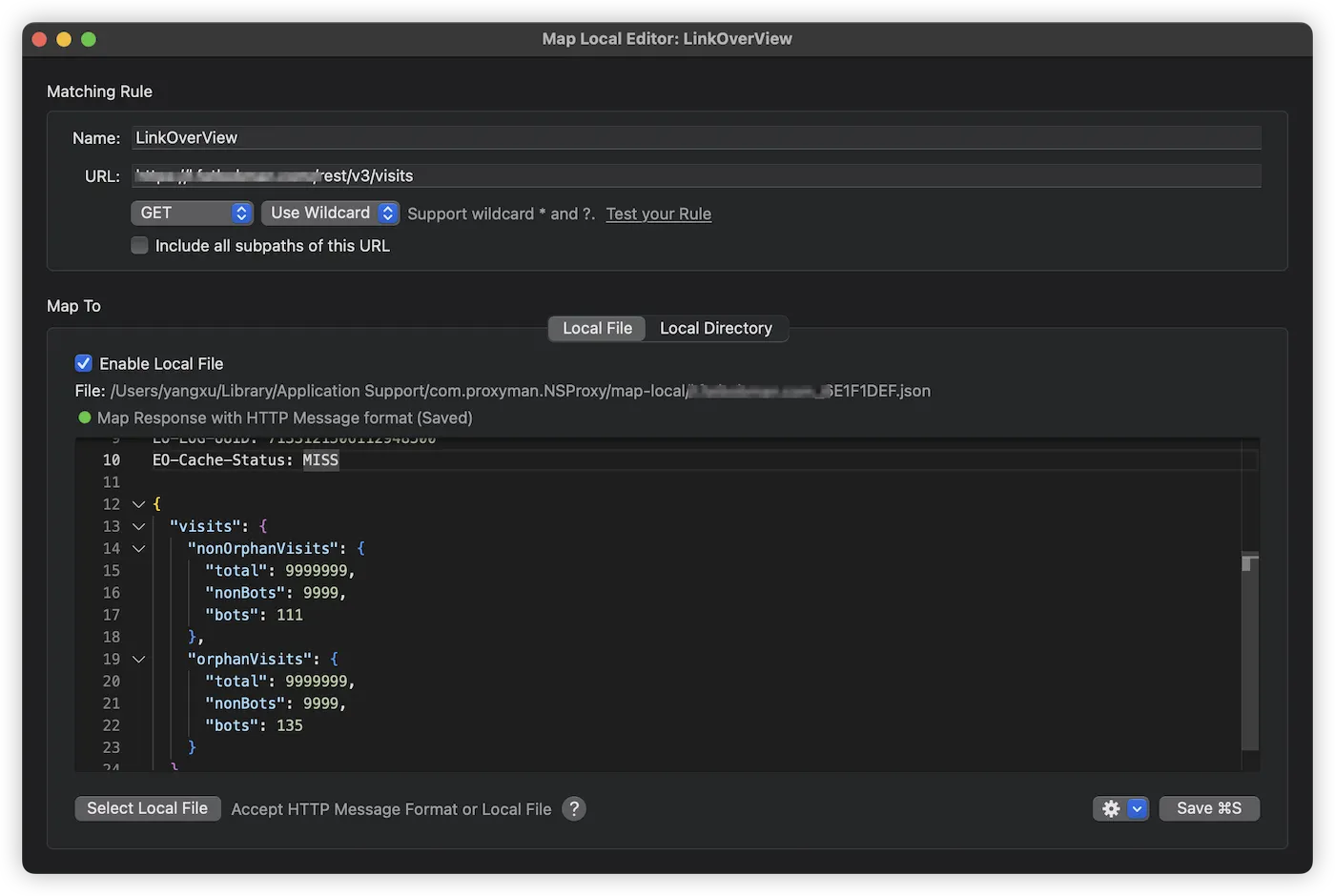
Map Local is suitable for static mocking, i.e., intercepting a request and directly returning a local file.
In the configuration panel, you can:
- Set the URL pattern to be mapped (supports regular expressions for flexible matching).
- Specify the applicable HTTP methods (GET, POST, PUT, etc.).
- Customize the returned data content and format.
Editing the Response Data
For JSON-formatted response data, Proxyman offers a particularly convenient editing experience:
- The editor automatically loads the last returned JSON data from the server as a template.
- You can directly modify field values, add, or delete properties.
- The editor supports syntax highlighting and formatting to reduce errors.
- All modified data is saved locally for repeated use.
Application and Advanced Features
After completing the Map Local setup, when the iPhone app sends a network request that meets the defined rules, Proxyman will automatically intercept the request and return your customized local data instead of forwarding the request to the actual server.
In addition to basic JSON data simulation, Proxyman also supports more complex data formats:
- Protocol Buffers (Protobuf) Mapping: With the appropriate schema configuration, Proxyman can automatically encode and decode Protobuf data, allowing developers to edit binary data as easily as JSON.
- Binary Data: Supports replacing responses with images or other binary content.
- Custom Status Codes and Headers: Enables simulation of various network conditions and server configurations.
These powerful data simulation capabilities make Proxyman an ideal tool for testing app behavior under various edge cases.
Summary and Reflections
Beyond exploring the network data of third-party apps as demonstrated in this article, network proxy tools like Proxyman have much broader application value in daily development work. They seamlessly support various physical devices, all Apple device simulators, and even Xcode’s live preview environment. The Map Local function is just one of many robust features Proxyman offers, including:
- Network Breakpoint Debugging: Similar to code breakpoints, this feature allows dynamic data modification—temporarily changing headers, bodies, and status codes.
- Custom Scripting: Use scripts to batch modify requests or responses.
- Automatic Code Generation: Automatically convert network requests into code implementations in various languages.
- Edit and Repeat Mechanism: Modify request parameters and repeat them to quickly test different scenarios.
In my development practice, I particularly appreciate the combination of the “repeat” function with automatic code generation. By repeating requests, I can accurately understand the functionality of each API endpoint. Then, using the code generation feature, I can convert the verified requests directly into executable code. With this workflow, I have successfully ported some functionalities—previously achievable only on dedicated iPhone apps—to the Mac platform, significantly enhancing my work efficiency.
Despite Proxyman’s powerful features, developers may still encounter various challenges during debugging. For example, in the aforementioned mock scenario, I faced a tricky issue: the target app used a less common data format, employing FlatBuffer, which is more efficient but harder to debug than JSON.
Fortunately, by using the official flatc compiler tool from FlatBuffer to analyze the data structure, I eventually pinpointed the data that needed modification. Although the process was somewhat complex, it successfully enabled the iPhone app to display the desired unique UI effect, confirming the effectiveness of network proxy debugging methods.
Network proxy tools have become indispensable assistants in modern mobile app development. With its user-friendly interface and powerful feature set, Proxyman is particularly suited for developers on the Apple platform. Whether analyzing third-party app behavior, debugging your own network requests, or creating test data to simulate various scenarios, it offers a reliable and efficient solution. These tools not only improve our development efficiency but also help us learn from the excellent practices found in other applications.